Home › Start here › Data protection › Logins ›
Logins
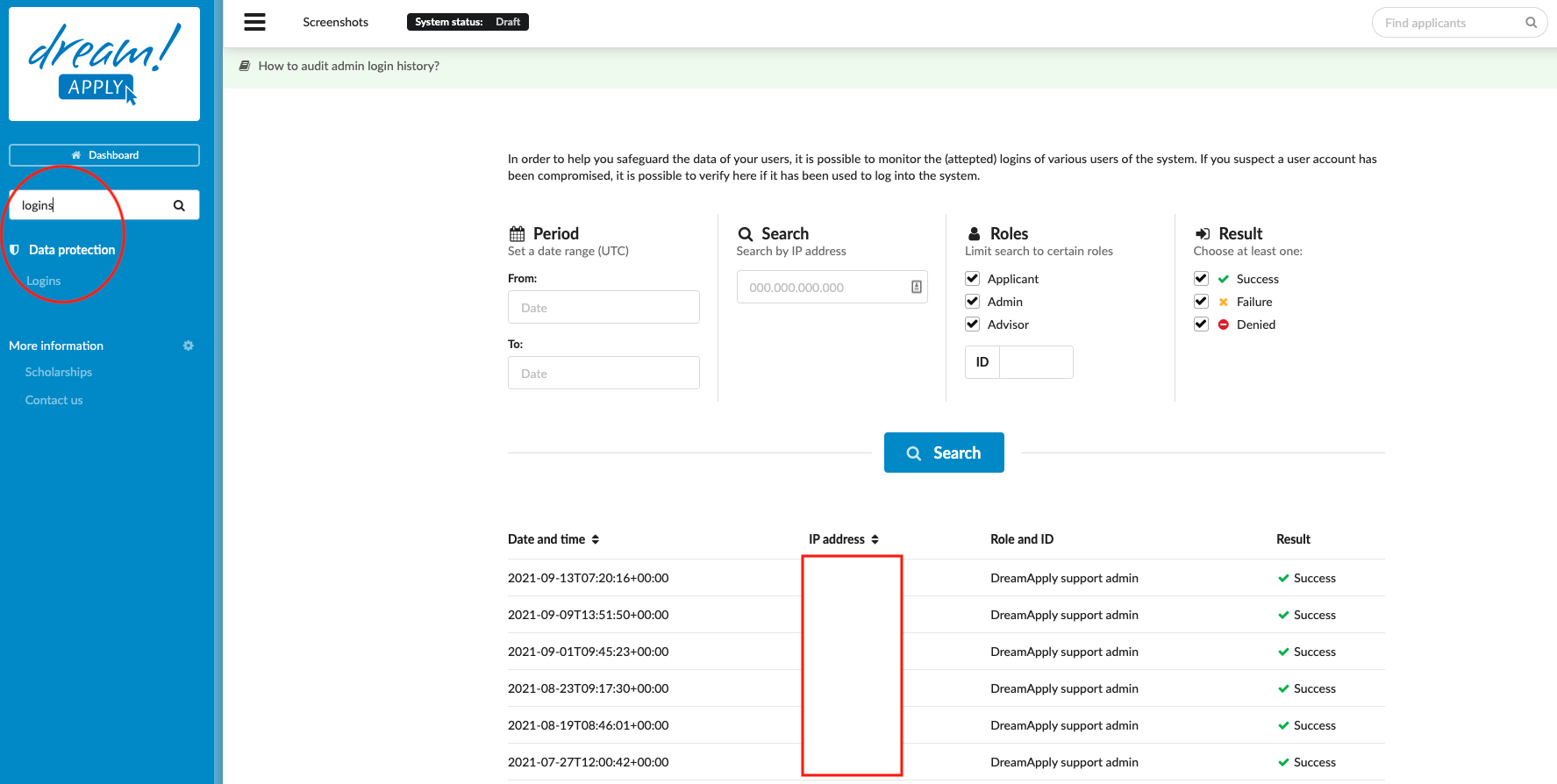
To help safeguard the data of your users, it is possible to monitor the (attempted) logins of various users of the system. If you suspect a user account has been compromised, it is possible to verify whether it has been used to log into the system.
Make sure you have:
-
the correct administrator permission (“instance”)
-
determined the time range for the logins to be investigated
-
determined the role of the user you whose login(s)/attempt(s) to be investigated
-
Log in as an administrator with the permission “instance” (included with the Role “Superuser”).
-
From the Main menu, go to Data protection > Logins.
-
Set filters:
-
Period – the range of times to be examined for logins
-
Role – used to narrow in on whether the interested login was done by either:
-
an applicant
-
an administrator
-
an agent
-
-
Result – used to narrow in on the result of the (attempted) login was either:
-
Sucess
-
Failure
-
Denied
-
-
-
Click on the “Search” button.
The detailed information of the logins matching the filters will be seen, including:
-
Date and Time
-
IP address
-
Role and ID
-
Result
Read more about how to delete the specific application
Read more about how to recover the data
Read more about “Shares” section